Lifecycle of Digital Identity Creation and Authentication
The complete lifecycle of digital identity creation and authentication, beginning with enrollment and ending with verified access to a relying party (RP). The process starts with an Applicant, an individual seeking to establish a digital identity. The Applicant interacts with a Credential Service Provider (CSP), which performs Enrollment and Identity Proofing. During this phase, the CSP verifies the applicant’s real-world identity and issues an authenticator or credential. Once verified, the Applicant becomes a Subscriber a user who now holds a valid credential tied to their identity.
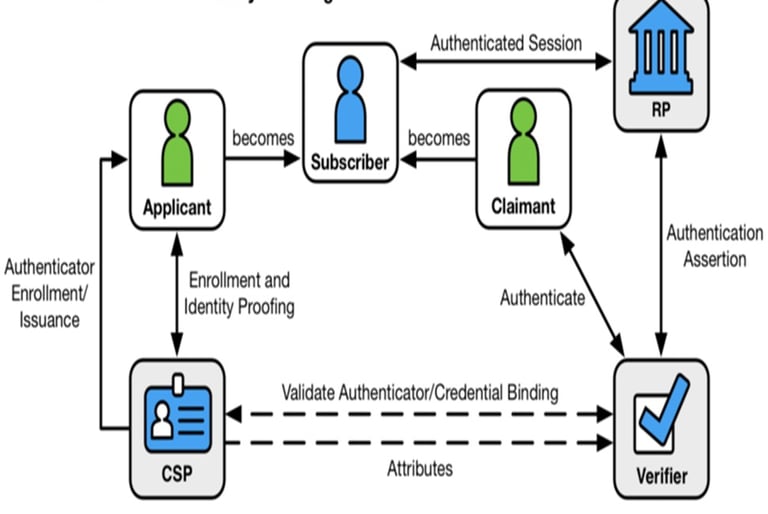
When the Subscriber attempts to access a digital service, they act as a Claimant. The Claimant authenticates by presenting their credential to a Verifier, which checks whether the credential is valid and correctly bound to the individual. This validation may involve cryptographic checks, shared secrets, biometrics, or multi-factor authentication.
Once authenticated, the Verifier sends an Authentication Assertion to the Relying Party (RP) the system or organisation the user wants to access. The RP trusts the assertion and grants the Claimant an authenticated session. Throughout the process, the Verifier may obtain additional attributes from the CSP to confirm identity bindings or provide required identity information to the RP.
Overall, the diagram shows how identity is established, authenticated, and trusted across systems. The roles of Applicant, Subscriber, Claimant, CSP, Verifier, and RP work together to ensure secure, validated, and reliable digital identity interactions.
Example 1
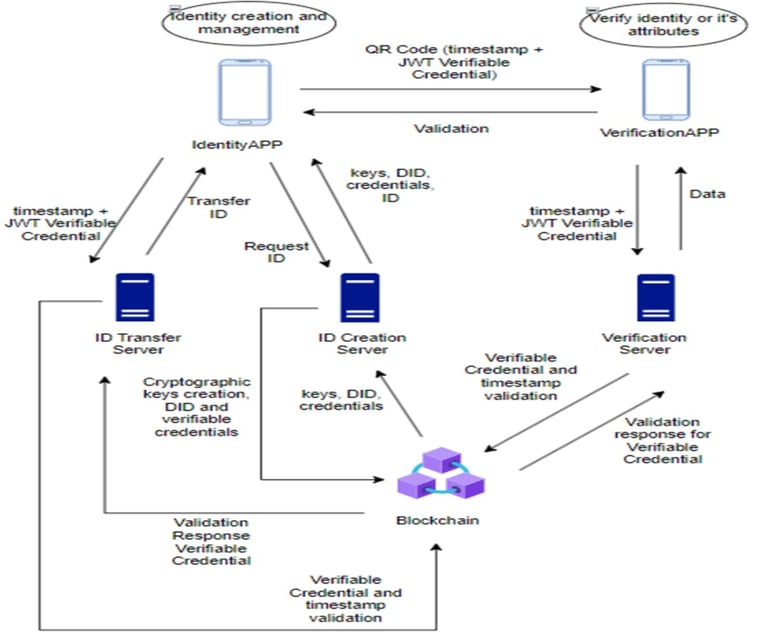
The diagram illustrates a decentralized digital identity lifecycle using DIDs (Decentralized Identifiers), JWT Verifiable Credentials, and a blockchain-backed validation process. Identity creation begins in the Identity App, where users request an identity from the ID Creation Server. The server generates cryptographic keys, a DID, and initial verifiable credentials. These are then stored and timestamped on the blockchain to ensure immutability, authenticity, and tamper-proof verification.
Once issued, the credentials can be transferred through the ID Transfer Server, which manages secure distribution of identity data. When the user needs to prove their identity or share attributes, the Identity App generates a QR code containing a timestamp and verifiable credential.
On the verification side, the Verification App scans the QR code and sends the credential to the Verification Server. The server checks the credential against blockchain records, confirming its validity, timestamp accuracy, and cryptographic integrity. It then returns a validation response, ensuring that no credential has been altered or forged.
This process enables secure, privacy-preserving identity verification without sharing unnecessary personal data. The blockchain acts as a trusted global ledger, while apps and servers exchange only the information required for secure validation.
Example 2
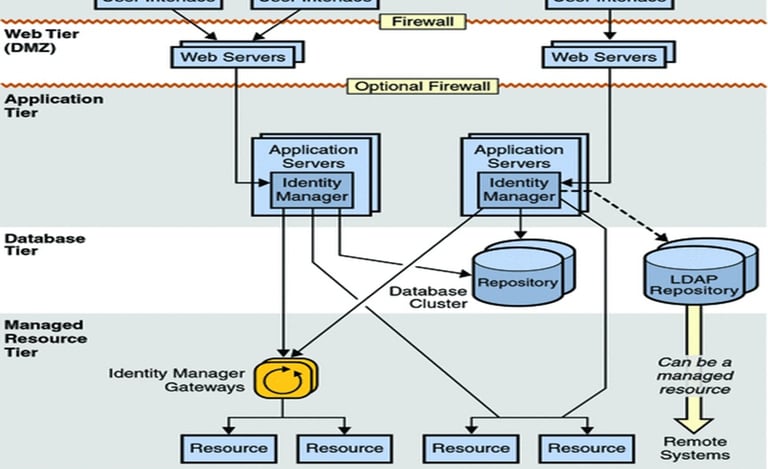
The diagram represents a multi-tier identity management architecture designed to support secure authentication and resource provisioning for both internal (intranet) and external (extranet) users. At the User Tier, end-users and administrators access the system through dedicated user interfaces. Their requests are routed to the Web Tier (DMZ), where web servers handle incoming traffic. Firewalls protect these interactions, ensuring that sensitive identity operations occur only within secured network zones.
Requests entering the Application Tier are processed by Application Servers containing the Identity Manager, which performs core functions such as authentication, authorization, provisioning, and policy enforcement. Internal and external user traffic may be separated by optional additional firewalls, improving security for external-facing services.
The Database Tier stores identity information in repositories. These may include standard relational databases as well as LDAP directories, which allow for hierarchical, attribute-based identity queries. Communication with LDAP can occur securely over SSL.
At the Managed Resource Tier, Identity Manager Gateways bridge identity services with various enterprise resources, applications, and remote systems. Through these gateways, identity managers can automatically provision, update, or revoke access rights based on organizational policies.
Overall, this architecture ensures a scalable, secure, and centralized identity management framework that supports multiple user types, integrates heterogeneous backend systems, and protects sensitive identity data across all tiers.
Get Started With Digital Trust
Take control of your digital identity today. Generate your secure, privacy-first DigitalTrust ID and enjoy one trusted identity for academic, professional, and online services worldwide.






Generate your DigitalTrust ID and take control of your secure digital identity.
For Institutions
Join a global ecosystem committed to security, transparency, and interoperability.
For Developers
Explore the open-source repository and contribute to building the future of digital identity.
DigitalTrust
OSDTIS (Open-Source Digital Trust Identification System) is a next-generation identification platform providing every user with one secure, reusable, and globally unique Digital Trust ID.
Contact
Newsletter
contact@inventivecreativity.org
+48 722 274 105
© 2025. - Inventive Creativity Foundation - All rights reserved.


QUICK LINKS
